Microsoft suffers data breach by hacking group LAPSUS$
Microsoft fall victim to notorious hacking conglomerate
WePC is reader-supported. When you buy through links on our site, we may earn an affiliate commission. Prices subject to change. Learn more
South-American Hacking group LAPSUS$, the same group behind the Nvidia hack a few weeks ago is back with another victim, Microsoft. As reported by Motherboard, the group alleges to have gained access to Azure DevOps source code, in addition to stealing data from the company. Instead of wanting to target consumer data, or installing ransomware onto the devices of employees at the business, LAPSUS$ is in the business of leaking source code and data that they then want to sell back to the company. But, it’s unclear if they’ve attempted to sell the data back to Microsoft.
But, one thing that they have done is leaked a screenshot from a Microsoft Azure DevOps account, which includes the source code repositories for countless projects such as Bing, Cortana, and more. But, the screenshot was quickly deleted after it was posted on their Telegram channel, an administrator commented ‘Deleted for now will repost later’. That’s exactly what they did, but this time, the group put it all back up as a torrent file, for anyone to download.
LAPSUS$ list torrent up for download
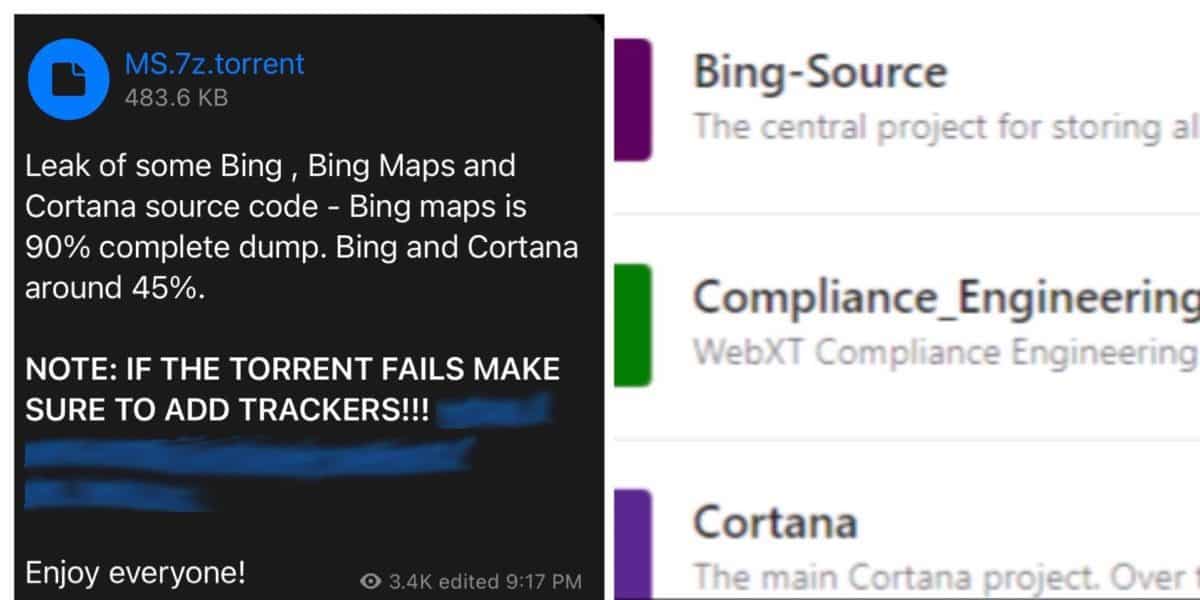
From the post listed by LAPSUS$, we can see that the group has begun to release some files they managed to obtain from the hack itself, seemingly in a move to intimidate Microsoft into bowing to whatever demands that they may be making for the information. In addition to this, having a public file release like this is bad news for Microsoft, as their competitors can easily read and reverse-engineer their technology, in a similar vein to what they did to Nvidia’s DLSS source code leaks.
According to Motherboard, the group was looking for employees inside Microsoft to work with them, in addition to a list of other companies such as Apple and IBM. A quote posted on the group’s Telegram channel states the following: ‘TO NOTE: WE ARE NOT LOOKING FOR DATA, WE ARE LOOKING FOR THE EMPLOYEE TO PROVIDE US A VPN OR CITRIX TO THE NETWORK, or some anydesk,’
They were explicitly looking into a backdoor into Microsoft’s network, disguised as a legitimate user, and they have clearly since been successful after the attack in reaching the information that they were looking for, potentially with the help of a mole at Microsoft, who helped the hacking group reach the servers and systems wherein their most valuable data lies.
This is just another to the laundry list of victims that have crossed paths with LAPSUS$, having previously hacked the Ministry of Health in Brazil, Electronic Arts, Samsung, Nvidia and potentially more. It’s clear from the way that the group communicates over Telegram that LAPSUS$ isn’t an organised group, but instead a collective of hackers looking to share their mutual gains from whatever spoils they pilfer from their targeted victims.
We’ve not directly confirmed that the Torrent that the group has uploaded is legitimate, but it’s clear that the group is intent on sharing whatever spoils they have gained. Curiously, many other groups of this nature do not use their access to these systems to steal and release confidential data, but instead, install ransomware onto the breached network’s systems and then attempt to directly extort the business via that method. One of the more dangerous things about LAPSUS$ is that the group is not afraid to widely share the stolen information, leaving the companies vulnerable to having their most confidential of documents out for the public, or even their competitors to see.
Emboldened by managing to compromise huge targets like Nvidia and Samsung means that this group is only growing ever more dangerous for tech companies, who want to be guarding their most precious of data closer than ever before. But, if the Telegram group’s call for moles in these businesses is true, they might have a much more difficult fight ensuring that these hackers do not get access to sensitive information.
Companies can choose to defend themselves against attacks such as this through the use of Red-Team penetration testing, which would be able to simulate an attack from within from a group such as LAPSUS$, and help identify any of the holes in their security, physical and digital. This is something that businesses are likely to be already doing, but they may wish to have a slight refresher, just to ensure they can identify any additional measures that hackers would have to get past before getting to access any further confidential data.
Microsoft makes a statement
Of course, when a company has had such an alleged data breach, they need to respond to ensure that they have a public stance about what may have happened, but the company doesn’t seem to acknowledge that it happened, or that any of their data is freely available to download on the Internet. This may be a PR move for Microsoft to save face in what could potentially be a pretty dire situation for them.
The company told Motherboard: ‘We are aware of the claims and are investigating.’
It’s likely that Microsoft might want to settle this one in private, while publicly acknowledging that something happened, but they might never release the full scope of exactly what might have happened to their networks, or a full list of what data was accessed on their networks unless it directly impacted consumer data and sensitive information.
Who will LAPSUS$ target next?
Going from the information that we already know, in addition to the fact that we understand that the group is clearly fairly new, but have successfully accessed a few high-profile targets, it only makes sense that after Nvidia and Microsoft, the group would go after another high-profile tech company like Apple, AMD, or another gaming brand. Regardless of where they might strike, this group has already proven that they are indeed incredibly dangerous, and are able to extort the most precious of information to high-profile tech companies. But, potentially knowing that they have a target on their backs, we might see these potential companies beefing up their network security in response to LAPSUS$.





